Difference between revisions of "How to dump RSA signed Insyde BIOS"
Falseclock (talk | contribs) (Created page with "== How to dump RSA signed Insyde BIOS == '''1'''. Take this BIOS.<br /> '''2'''. Unpack with any unzip software<br /> '''3'''. Find platform.ini file<br /> '''4'''. Edit foll...") |
(Several grammar, spelling, and English corrections.) |
||
| (5 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Starting from 2012, Insyde Corp. implemented RSA algorithm to encrypt their BIOSes in an effort to avoid modding. To unpack such a BIOS with PhoenixTool is impossible. However, we are 100% certain that the BIOS ROM stored in the motherboard is a decrypted variant. The easiest way to get it - make a backup of current BIOS before flashing with the new one. But we can also flash with a modded BIOS version over the same BIOS version number. | |
| − | '''1'''. Take | + | |
| + | Here are the instructions: | ||
| + | |||
| + | === Flasher (platform.ini) way === | ||
| + | |||
| + | '''1'''. Take your current executable BIOS flasher.<br /> | ||
'''2'''. Unpack with any unzip software<br /> | '''2'''. Unpack with any unzip software<br /> | ||
| − | '''3'''. Find platform.ini file<br /> | + | '''3'''. Find "platform.ini" file<br /> |
| − | '''4'''. Edit following lines | + | '''4'''. Edit following lines with Notepad |
<tt>[BackupROM]</tt><br /> | <tt>[BackupROM]</tt><br /> | ||
<tt>Flag=1</tt><br /> | <tt>Flag=1</tt><br /> | ||
| − | <tt>FilePath= | + | <tt>FilePath=C:</tt><br /> |
| − | <tt>FileName=<put | + | <tt>FileName=<put BIOS name here>.BIN</tt><br /> |
| + | '''5'''. Flash the same BIOS again with the modified platform.ini<br /> | ||
| + | '''6'''. After reboot you will find dumped current BIOS on C drive<br /> | ||
| − | ''' | + | === UEFI way (EFI system partition) === |
| − | ''' | + | |
| + | On some new platforms (for example HP Envy 17 (17-j005tx) '2013), the BIOS reading (backup) feature is disabled. In such case, flasher will show the following error message '''IHISI: flash read error in SMI!''' and the system will hang (on some notebooks, you might even need to unplug the power and remove the battery to shutdown the system). | ||
| + | [[File:Flash read error small.jpg]] | ||
| + | It doesn't seem to depend on Windows version or type (x64/x86), even WinPE recovery disks won't help. | ||
| + | |||
| + | However, in most such cases, the flasher will not update the BIOS directly, but will use the UEFI BIOS update procedure (after rebooting). The new BIOS is copied (in unencrypted form) to the UEFI partition, so we just need to find it there. | ||
| + | '''EFI System Partition''' is not normally visible in Windows and you will not be able to assign a disk letter to it using the standard Disk Manager. However, the following command in console under Administrator account (Run as Administrator - elevated command prompt is required) will help (mounting EFI partition as disk X:):<br/> | ||
| + | <tt>mountvol X: /S</tt><br/> | ||
| + | You might want to run this command from some console file manager (like FAR, http://farmanager.com/) or run your file manager side-by-side under Administrator account, since X: disk won't be visible/accessible otherwise. | ||
| + | Then, walk through disk X: (just don't delete or modify anything) looking for copies of your unencrypted BIOS. For HP Envy 17 they were found in '''X:\EFI\HP\BIOS\Current''' folder, in form of '''01966.bin''' file (instead of original encrypted 01966.fd). | ||
Latest revision as of 18:32, 18 August 2014
Starting from 2012, Insyde Corp. implemented RSA algorithm to encrypt their BIOSes in an effort to avoid modding. To unpack such a BIOS with PhoenixTool is impossible. However, we are 100% certain that the BIOS ROM stored in the motherboard is a decrypted variant. The easiest way to get it - make a backup of current BIOS before flashing with the new one. But we can also flash with a modded BIOS version over the same BIOS version number.
Here are the instructions:
Flasher (platform.ini) way
1. Take your current executable BIOS flasher.
2. Unpack with any unzip software
3. Find "platform.ini" file
4. Edit following lines with Notepad
[BackupROM]
Flag=1
FilePath=C:
FileName=<put BIOS name here>.BIN
5. Flash the same BIOS again with the modified platform.ini
6. After reboot you will find dumped current BIOS on C drive
UEFI way (EFI system partition)
On some new platforms (for example HP Envy 17 (17-j005tx) '2013), the BIOS reading (backup) feature is disabled. In such case, flasher will show the following error message IHISI: flash read error in SMI! and the system will hang (on some notebooks, you might even need to unplug the power and remove the battery to shutdown the system).
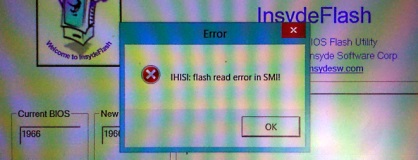 It doesn't seem to depend on Windows version or type (x64/x86), even WinPE recovery disks won't help.
It doesn't seem to depend on Windows version or type (x64/x86), even WinPE recovery disks won't help.
However, in most such cases, the flasher will not update the BIOS directly, but will use the UEFI BIOS update procedure (after rebooting). The new BIOS is copied (in unencrypted form) to the UEFI partition, so we just need to find it there.
EFI System Partition is not normally visible in Windows and you will not be able to assign a disk letter to it using the standard Disk Manager. However, the following command in console under Administrator account (Run as Administrator - elevated command prompt is required) will help (mounting EFI partition as disk X:):
mountvol X: /S
You might want to run this command from some console file manager (like FAR, http://farmanager.com/) or run your file manager side-by-side under Administrator account, since X: disk won't be visible/accessible otherwise.
Then, walk through disk X: (just don't delete or modify anything) looking for copies of your unencrypted BIOS. For HP Envy 17 they were found in X:\EFI\HP\BIOS\Current folder, in form of 01966.bin file (instead of original encrypted 01966.fd).
